By bad actors, I don’t mean the cast of your favourite soap opera, but instead people who have ulterior motives which could cause you harm. Such as the government collecting your metadata, your ISP selling your private browsing information, or a popular free web service scanning your online information. In the latter category is definitely free email services such as Gmail, Microsoft, and Yahoo. Their business model is increasingly centered on advertising, so in order to send you the most appropriate adverts you are most likely to click on, they scan your emails. They say they do this to root out malware, but in reality, they want to see your plans and your interests, so they know what adverts to send you. Some people may find this useful, but at the end of the day, it is a huge and unjustifiable breach of privacy. The only way to get companies to stop doing this is to make it extremely difficult or downright impossible for them to read your emails.
The Simple Solution
What is the solution? Well as the saying goes “if you are not paying for the product, then you ARE the product”. Which means if you pay for email, you have more of a chance of privacy.
In this scenario, the ideal solution is to move to Protonmail. There are many things going for it. One, it is based in Switzerland and has no servers in the US, so it is outside the legal jurisdiction of the Patriot Act. Secondly, each email is heavily encrypted by PGP keys (more on that later), and third, you need two passwords to gain access – a regular password and then an inbox decryption password. The downside though (and there always is one with everything in life) is that Protonmail is still very much a work in progress. The Protonmail team is working very hard and fast (they have even introduced a Virtual Private Network app for their paying customers), but compared to say Gmail, Protonmail has many glaring drawbacks which may irk some and prevent many from moving their email over 100%. Paying for Protonmail gives you some nice extra features, but it still isn’t exactly there yet in my opinion. So if you are totally wedded to your Gmail, and can’t bear to part with it, what is the alternative?
OpenPGP
PGP stands for “Pretty Good Privacy” and was developed by a man called Phil Zimmermann in 1991. PGP is not free – it is proprietary software owned by the Symantec Corporation, but in the late 1990’s, a free open-source version was created, called OpenPGP. Wikipedia has some good background information on it here. PGP involves the automatic generation of two keys – one public and one private. The public key is made public and people use it to send you encrypted emails. The private key is kept private by you and is used by you to decrypt the email sent to you. As long as you never reveal your private key to anyone, the emails are theoretically unbreakable.
One method of installing OpenPGP is to install an offline mail client such as Microsoft Outlook, Mozilla Thunderbird, or Apple Mail. Then install either GPG4win (Windows) or GPG Suite (MacOS). Thunderbird users can also install a Firefox extension called Enigmail, which does the same thing.
OpenPGP Browser-Based Alternatives
But what if you don’t like or don’t want to use an offline client? What if you are stubborn and you want to stick to browser-based email? In that case, there are browser plugins which can do the job for you. We are now going to run through 3 possibilities and see which one does the job best. They are all open-source, meaning the code can be freely viewed by anyone to test its integrity, the services have complete transparency as a result, and anyone can suggest improvements. Remember though that the person you are sending the email to must also have a PGP key.
Mailvelope (Chrome & Firefox)
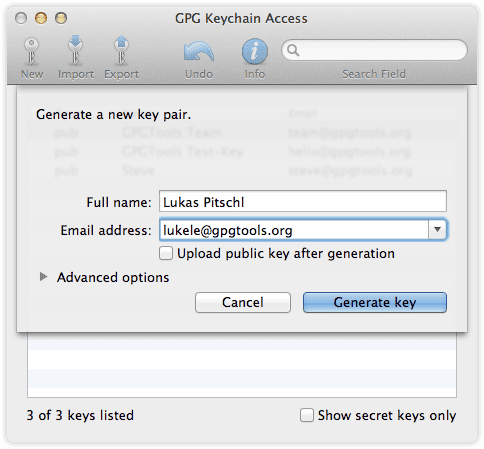
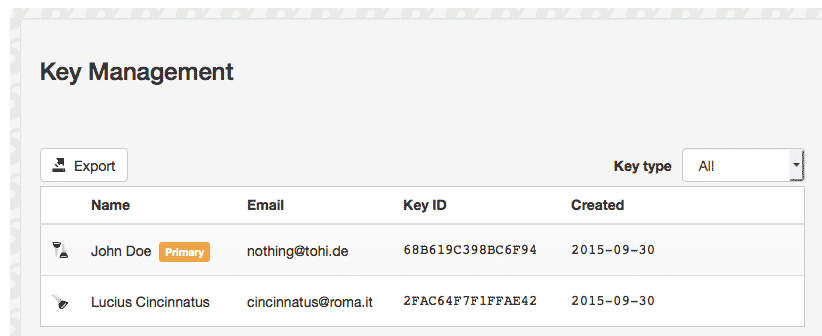
In his new book, “The Art Of Invisibility“, infamous hacker and former “social engineer” Kevin Mitnick recommends Mailvelope in his chapter on email encryption. Once you have installed Mailvelope, click on the padlock icon to the right of the URL browser bar. Then click on “Options“. In the “Key Management” section, follow the process to generate new public and private keys (if you don’t already have them). If you do, you can import them. When this is done, your keys will now be in Key Management. You can freely distribute your public key to everyone, but keep the private one completely concealed.
What is slightly different about this service is that it insulates your drafts from the webmail service by forcing you to write your drafts inside an external editor controlled by Mailvelope.
When you have finished the email, choose the key to encrypt the email, and when it is encrypted, it will be copied over to the webmail service for sending.
Streak (Chrome)
Although Mailvelope has a lot to recommend itself for, I have a bit of a positive bias for Streak, because I already use this app extensively for scheduling emails to be sent, and emails to be snoozed for later (virtually identical to how Boomerang works). I hate to use a new app when one I am already using does the same thing, so I am inclined to use Streak for email encryption as well. But that’s just me. The one downside is that Streak is for Google Chrome only, so Firefox users are out of luck.
Once you have installed it, a small padlock will appear next to the Gmail “Compose” button. Clicking the padlock will ensure that no drafts of the email will ever appear on Google servers. Once you have written your email, you will be asked for a password, which the other person is expected to know. If not, you should find a separate and secure way of telling them the password (encrypted instant messaging, for example).
When a password has been entered, your email will be encrypted and sent. This is what your recipient will see.
Once they enter the password, the text will change to plain readable text.
CryptUp (Chrome & Firefox)
After installing the extension, you need to provide CryptUp with permission to access your Gmail account. Upon doing so, you then need to generate or import your public and private PGP keys. Just follow the easy-to-understand step-by-step process. Once you have set everything up, a new “Secure Compose” button will appear. So you can send both encrypted and unencrypted messages.
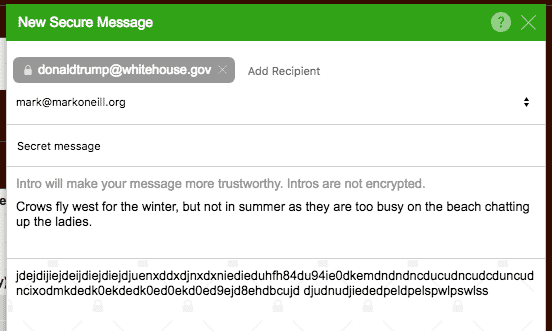
What is really good about CryptUp is that if the other person does not have a PGP key, you can still send them the email using a one-time password. But for more long-term correspondence, they should set up PGP keys.
Another great feature is the ability to add an unencrypted “intro” to the email. If the other person perhaps does not realize the encrypted message is from you, you can add a message establishing your bona fides. Or attach a pre-arranged note like how spies know to trust one another when they meet – “the crows fly west for the winter….yes, but not in summer”).
Conclusion
It probably seems to most people that email encryption is a pain in the neck, therefore it just gets skipped. But you shouldn’t do this. Even though you may live by the mantra “I have nothing to hide”, your privacy is still paramount, and nobody has the right to read your private communications without legal authorization. Hopefully these browser plugins have demonstrated just how easy it actually is to get started on it. The only remaining difficulty is persuading the other person that it is necessary for them to set it up too and that you are not a tin-foil hat kind of guy. Good luck with that. “wrapped in tinfoil” by mrwynd is licensed under CC BY 2.0 Δ Contact Us :- trendblog.guest@gmail.com